Recent searches
Search options
#openvpn
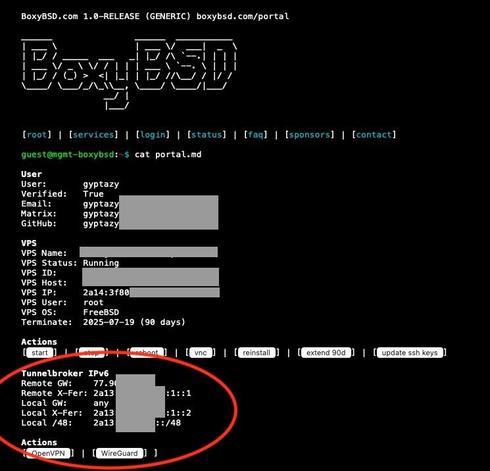
Would you be interested into an alternative #IPv6 Tunnelbroker service? Hosted and located in Germany, offering free IPv6 subnets (not sure about sizes, sth. between /64 - /48) that can be used by #SIT, #GRE, #OpenVPN or #Wireguard tunnels. Currently, this is already available but only for @BoxyBSD users.
Does anyone know how this new SSL cert expiry date thing is going to affect things like user authentication with SSL certs, i.e. for openvpn.
If we're running our own CA, can I get safari, chrome et al to accept longer cert expiry?
@JessTheUnstill @Pibble
And yes, I treat all devices as insecure and would rather invest the time and effort needed get #TechIlliterates up to speed on the #OfflinePGP method!
- Sounds cumbersome, but when your threat model literally goes against the #1 #Hacking #Regime (#USA) with more #Exploits stockpiled than any hacking forum (cuz #NOBUS doctrine), you gotta have to upgrade.
Given the cheapness of storage (legitimate 1TB microSD cards exist and they ain't 4-digit items!) I'd legitimately look into #OTP #encryption and (IF I had the €€€€€€ to do so!) would even sponsor implementing it in #OpenVPN, #WireGuard and #OpenSSH (for #SSH-Tunmeling).
- The #US is a #RogueNation with a Rogue Government! The sooner we accept this reality the sooner we can not only adjust to it but act accordingly…
I sincerely wish y'all could legitimately call me a tinfoilhat but so far I've been proven right all the time...
#DerStandard:
"
Trumps Kürzungsrausch gefährdet für das Internet wichtige Open-Source-Projekte
Die neue US-Regierung entzieht dem Open Technology Fund die Mittel. Von diesem sind unter anderem Let’s Encrypt, Tor und F-Droid finanziell abhängig. Der OTF hat Klage eingereicht
"
https://www.derstandard.at/story/3000000263520/lets-encrypt-tor-trump-kuerzungen-gefaehrden-fuer-das-internet-wichtige-open-source-projekte?ref=article
30.3.2025

I just received a concerning email from the OTF (@opentechfund.bsky.social) stating that a major source of their funding is in jeopardy.
If you care about open-source, anti-censorship, or the open internet, please consider supporting one of the projects they fund.
#FOSS #OpenSource #TechNews
#USPol #Politics #News #PoliticalNews
#NetNeutrality #EFF
#Wikimedia #Signal #SignalApp
#TOR #TAILs #OpenVPN #VPN #LetsEncrypt #HTTPS #SSL
#Censorship #AntiCensorship
Warum noch mal war unsere kritische Infrastruktur im Netz, wie #letsencrypt oder #OpenVPN, von der US-Regierung abhängig?
Irgendwann braucht man nach #Heartbleed und #GnuPG-Krise auch nicht mehr Snowden zitieren, wenn die einzige Konsequenz, die man da nicht gezogen hat, die ist, dass Open Source-Entwicklung auch Geld kostet.
Und dass man das am besten auch nicht allein einer alle vier Jahre wechselnden Regierung überlässt.
Und Gott sprach: "Lächle, es könnte schlimmer kommen."
Und er lächelte und es kam schlimmer:
Die US-Regierung unter #Trump hat Fördermittel für den Open Technology Fund (#OTF) blockiert.
Betroffen sind u.a. #LetsEncrypt, das #Tor-Netzwerk, #OpenVPN und F-Droid.
Der OTF klagt nun auf Freigabe der Mittel. Rund 650.000 $ fehlen allein für laufende Kosten im März.

Es ist zum heulen mit anzusehen, in welcher Geschwindigkeit die Welt um einen zerstört wird.
#letsencrypt #fdroid #openvpn #opentechnologyfund
Ist waybackmachine noch da?
#archiveorg
#Tor
#LetsEncrypt
#OpenVPN
#FDroid
#OTF
US-Behörde stoppt Gelder für Let's Encrypt und Tor ‒ Open Tech Fund wehrt sich | heise online
https://www.heise.de/news/Nach-Trump-Dekret-Kampf-um-US-Foerdermittel-fuer-Tor-F-Droid-und-Let-s-Encrypt-10328226.html

@StaceyCornelius In the past I did configure seperate systems for clients so they can travel without fuss regardless if "P.R." #China or #Russia or the #USA or #KSA...
- The trick is to never have anything on your device and have a dedicaded burner!
Using @tails_live / @tails / #Tails and @torproject / #TorBrowser and when that's not an option, a #SSH-Tunnel / #OpenVPN or #WireGuard-#VPN to be able to #VNC into a machine.
- Remember: They can only extract data that was saved on a machine!
CONSIDER THE #US ENEMY TERRITORY AS IN "If you wouldn't enter #NorthKorea, then why would you enter the USA?"
Endlich Mal die Muße und Motivation gefunden, mir seit Corona wieder ein #VPN in die heiligen Hallen meiner privaten Infrastrukturverbrechen zu bauen.
Früher hab ich #openvpn per TCP benutzt, weil sich das gut per ipv4 auf meinen ipv6 Ingress umbiegen ließ.
Aber 2025 ist ja #WireGuard all the rage. Also ipv6 udp und Abfahrt. D1 Netz kann ja v6.
Dank #opnsense und guter Doku ging das relativ easy. Und ist auch angenehm flott.
Mal sehen ob ich die Kids jetzt dauerhaft umleite für adblocking etc.
#Synology: #OpenVPN eingerichtet, Firewall Ports konfiguriert, FRITZ!Box forwarding und dyndns etc. #VPN klappt, ping auf lokale IP auch aber #ssh nicht weil Synology das nur noch für die Admin Gruppe erlaubt?! Muss ich „#git“ zum Admin machen? Örgs… no!
Zugriff über WebDAV? Noch ne B(K)rücke? Hat nicht sofort geklappt. Erstmal aufgehört.
Das muss doch einfacher gehen … (2/2)
Am not convinced about such a setup with an orchestration server. The OpenVPN setup seems more straight forward to me (for my scenario).
I would need to replace the ASUS routers with other hardware (mini-pc or something) with Linux/OpenVPN, but other than that, it all works fine.
The only thing that would be better with Tailscale/Netbird, is that no port-forwarding is needed anymore.
I only have the requirement to connect to the remote networks, the remote networks must not be able to connect to mine.
Would appreciate your input/thoughts/experience. 
2/2
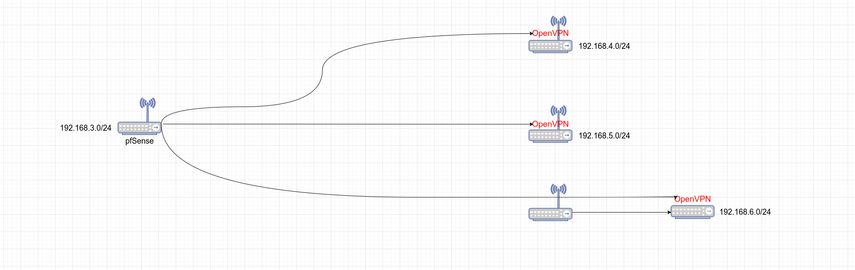
Have finally taken some time to read up on current VPN options in homelabs, as my involved hardware is no longer supported.
I have quite a few connections from my network to remote networks at family/friends for IT support (around 10). I connect from my pfSense via OpenVPN to OpenVPN server running on ASUS routers, flashed with Merlin firmware. The models are no longer supported, so am looking for alternatives.
Some of these ASUS routers function as a router plus the OpenVPN server, some routers just serve as an OpenVPN server.
Have checked Tailscale (with Headscale as I do not want to rely on 3rd parties)) and Netbird (apparently possible to selfhost).
In both setups every single device need to be configured separately and not all devices have native clients. Tailscale seems to have an option for "exit nodes" so the network where the device is in, is also reachable.
1/2
#SysadminLife pondering…
Given
- Remote #Debian/#Ubuntu server
- can‘t be accessed from internet
- behind (CG-)NATv4, no IPv6
- can reach any outside tcp/udp port
- A network under my full control
- Firewall can do: #IPSec, #Wireguard, #OpenVPN, #Tailscale/#Headscale Client
- I can self host any opensource service/container, and expose it
Challenge
- Make services on that server accessible TO my network
- server MUST NOT reach ONTO my network
- No 3rd party service dependence